Not known Incorrect Statements About Charlotte It Outsourcing
Table of ContentsWhat Does Charlotte It Outsourcing Mean?It Consulting Charlotte Can Be Fun For AnyoneWhat Does It Services Charlotte Mean?The Definitive Guide for It Services CharlotteThe 45-Second Trick For It Support CharlotteLittle Known Facts About Managed It Services Charlotte.It Support Charlotte Things To Know Before You BuyFacts About It Services Charlotte Revealed
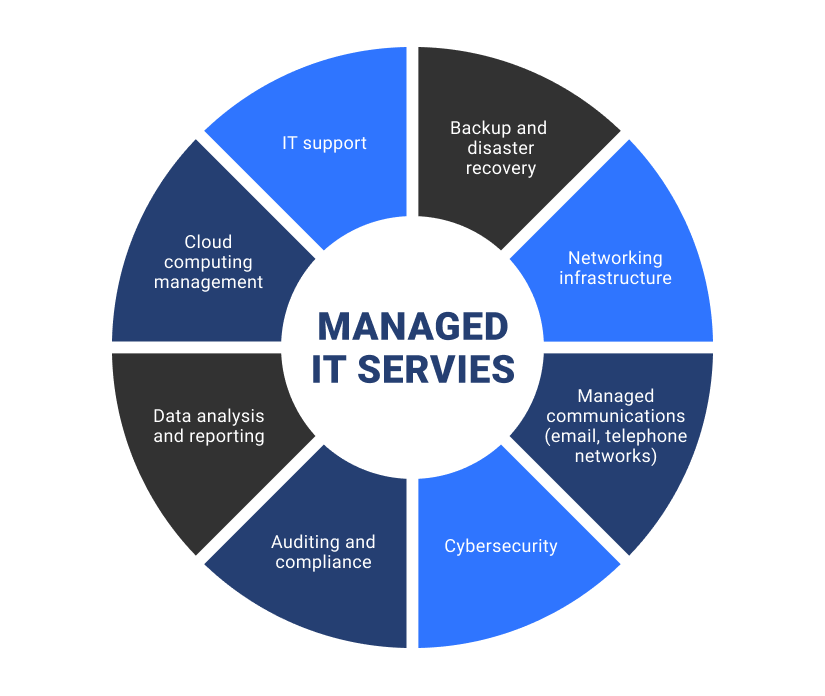
With so many functions to fill up, choosing an MSP can feel overwhelming. Attach, Wise uses easy-to-understand bundles for this solution, and we're always happy to aid, even if you have general inquiries.A service technician would certainly come out to fix handled computer system systems only after they quit working. Usually, this technician coincided person that constructed or set up the computer system. From this factor, computer system manufacturing remained to expand to the factor where big firms like IBM, Microsoft, as well as Apple took over.
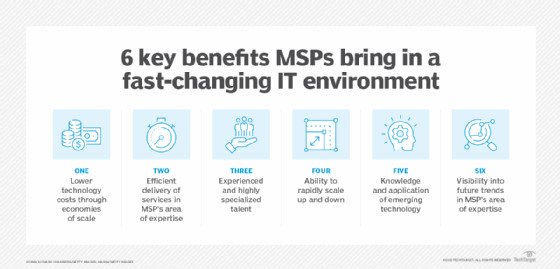
MSPs have actually come a lengthy means from the early days of handled IT services. Now, these specialists have a variety of IT competence as well as tools to settle issues effectively. MSPs can offer "white handwear cover" service to even more clients than ever before using these modern-day and also ever-evolving procedures, devices, as well as software application.
It Company Charlotte - Truths
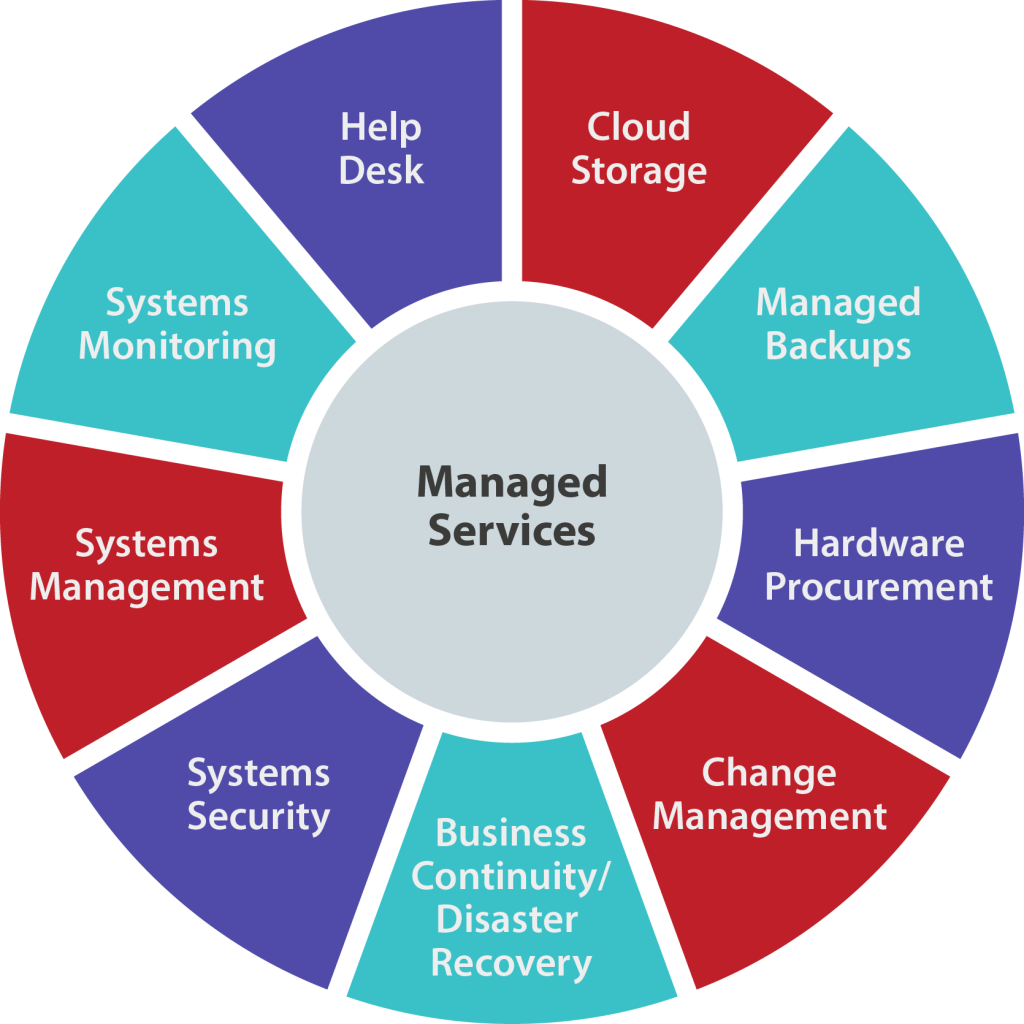
Whatever from task administration and assistance desk solutions to reporting and also billing all happens in one area, assisting MSPs save time and also do more for their clients. Various other tools aid MSPs provide handled IT services 24/7/365.
In the end, these devices permit MSPs to keep client expenses down while supplying better service, allowing clients to run their companies and live their lives with satisfaction. MSP services are typically supplied at a flat, persisting price in tiered degrees. As solution degrees boost, customers obtain greater automation and also management per their defined solution level agreement.
Handled IT solutions are frequently sought-after. Understanding the sector's framework, history, as well as terms is important to offering customers with the solution they deserve. The space can be competitive, but it's absolutely nothing to be intimidated by. Partnering with the right MSP supplier can make all the distinction. Connect, Wise can offer you a full suite of MSP software platforms and also tools.
Facts About It Company Charlotte Uncovered
We're here to see you prosper in this sector, so do not hesitate to connect to us any kind of time as well as leverage our years of competence to raise your MSP business. You can likewise take advantage of the expertise of your peers fellow professionals within the MSP sector.
The tools to service changing systems have had trouble catching up. Firms taking care of little networks in the past were impeded by a lack of devices to assist with troubles.
The smart Trick of It Consulting Charlotte That Nobody is Discussing
It was back to the break-fix technique. Together with this repairing ineffectiveness, backup issues and other mistakes remained to occur. The only professional examination of backup systems occurred on the check-up browse through. This could result in days or more of missed out on backups. it support charlotte. This system was likewise susceptible to human mistake.
As big companies started to have huge networks, they led the means for managed solutions. IT vendors started to add new and better means for systems to indicate troubles as early as feasible.
5 Simple Techniques For Cyber Security Charlotte
That information gets stored as historical data. Customers have access to this click for info information and also can utilize it to evaluate patterns in performance connected with a specific tool or database. Therefore, they can make informed decisions about future IT needs. Both local business owner and also inner IT personnel would a lot rather concentrate on revenue-enhancing jobs like item growth or boosting operations.

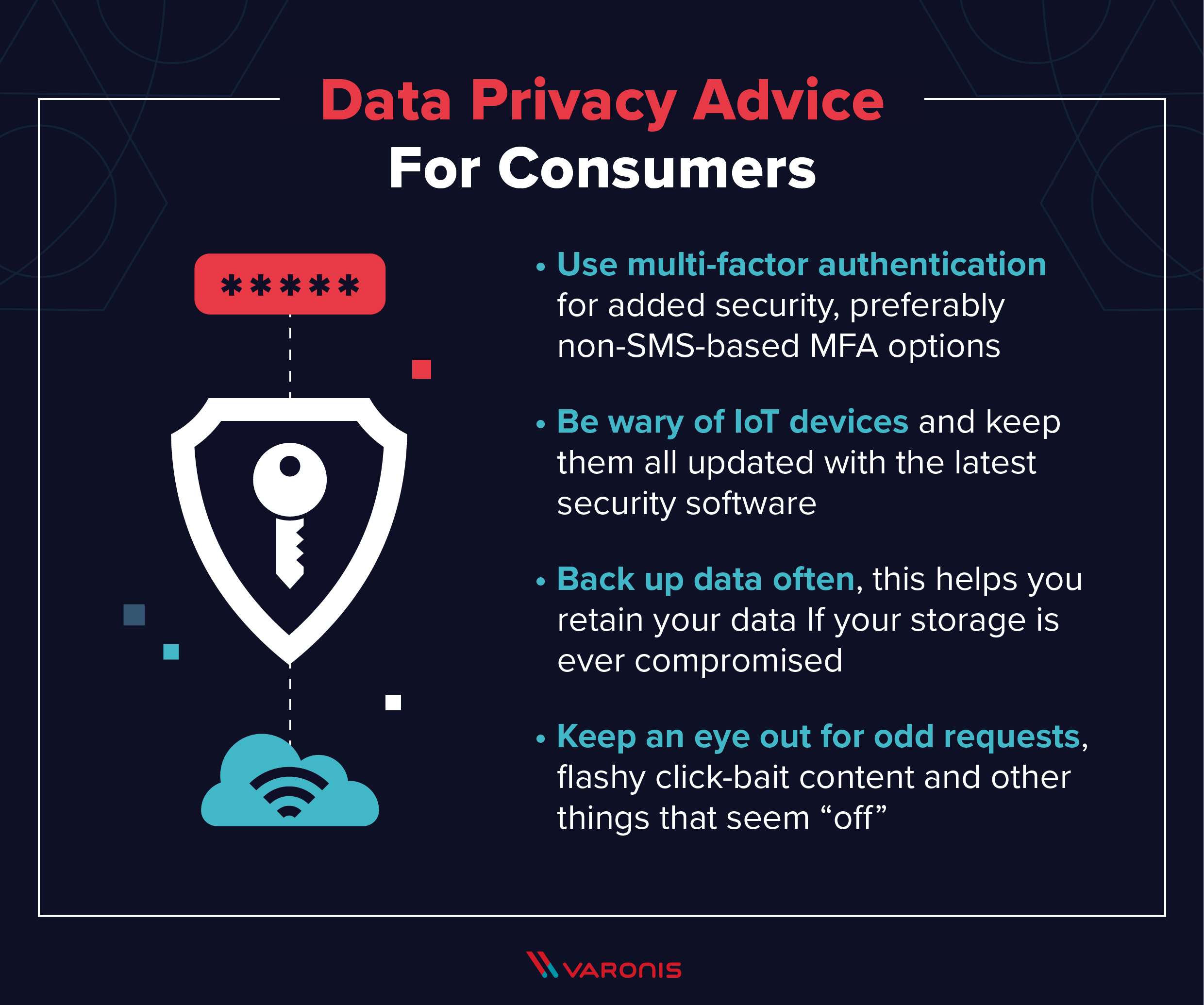
Typically misportrayed as a hazard to interior IT staff, Bonuses MSPs can instead ease them of mundane maintenance, recurring tracking jobs, and also daily functional responsibilities. When IT staffs are also hectic with firefighting duties, patch monitoring is something that has a tendency to fall to the back heater. This can leave a company at risk for downtime, safety and security susceptabilities, and also incidents that a supplier may not sustain when spots are too way out of day.
Should Bob the company owner really be spending any kind of time on tech issues? A handled service business can avoid issues before they occur, and manage most services from another location.
The Of Charlotte It Outsourcing
The expense of managed solutions and renting out hardware from your carrier instead of acquiring (understood as Hardware-as-a-Service [Haa, S] can also consider as a business/operating cost. This allows most firms to subtract costs from their tax obligations to conserve much more cash. These deductions aren't readily available with the old break-fix version.
Depending upon the services consisted of, rates is typically based on the variety of gadgets took care of or variety of customers. This makes it simple for a business to obtain the specific solution they need, without spending for more than is necessary. Functions like on-site assistance and also gadget leasing can even be added to supply a comprehensive support package.
Organization owners do not have time for this! If they do the work too well, they will go out of organization, which occurs to concerning 80% of all little IT firms.
Unknown Facts About It Consulting Charlotte
As a result, they can make enlightened choices concerning future IT requires. Both business owners as well as internal IT staff would certainly a lot rather focus on revenue-enhancing tasks like product growth or improving procedures.
Usually misportrayed as a threat to internal IT staff, MSPs can rather soothe them of ordinary maintenance, repetitive surveillance tasks, and daily functional obligations. When IT staffs are as why not try this out well hectic with firefighting obligations, patch administration is one thing that tends to be up to the back heater. This can leave an organization in jeopardy for downtime, security vulnerabilities, as well as occurrences that a vendor might not support when spots are as well much out of date.
As well as when he or she remains in monitoring, the expense is also higher. Should Bob the company owner actually be spending any type of time on technology concerns? Making use of break-fix assistance, rush charges and also after-hours/weekend support to handle emergency situations accumulates. A managed service firm can avoid issues before they occur, as well as manage most solutions remotely.
Not known Details About It Support Charlotte
This enables most companies to deduct costs from their tax obligations to conserve even more money. These reductions aren't readily available with the old break-fix design.